Security
Google explains how your data is collected and protected
Find out what data is collected, how it is used, and how we can stay in control
Having a connected life makes it permeable for tech giants such as Google, Apple, Facebook, and Microsoft to know more about us. The issue of privacy has become one of the major concerns today.
Just like gold, data has been officially the essential currency that companies mine. At the cost of our personal information, technology progresses. But then, we’re left to fend for ourselves. So how do we know our data are safe and protected?
Google’s Product Manager for Privacy and Data Protection, Greg Fair, stated that in 2020, the searches for ‘online privacy’ grew by more than 50 percent. At the same time, 81 percent of consumers are now concerned about their data.
This is why Google launched a privacy comic book as part of its commitment to educate the public about how the company protects people’s data. But more than that, I recently learned Google’s responsible data practices and their advanced security technology through a roundtable with fellow journalists from the Asia-Pacific region.
So, let’s talk about Google’s transparency on what data is collected, how it is used, and how we can stay in control.
Location information
Ever wonder how you can navigate your short-distance travels easily by knowing which roads to skip due to traffic congestion? That’s all because Google Maps collect anonymous data to generate information that helps other users understand what’s going on around them.
This set of anonymized user data are personalized and helps improve products. For instance, some places get relevant information whenever a user provides personalized details about a certain restaurant.
While it’s great to be able to contribute to any improvement of a product, Google reminds people that they’re still in control. You can still turn off your location history, or have it automatically deleted after three or 18 months.
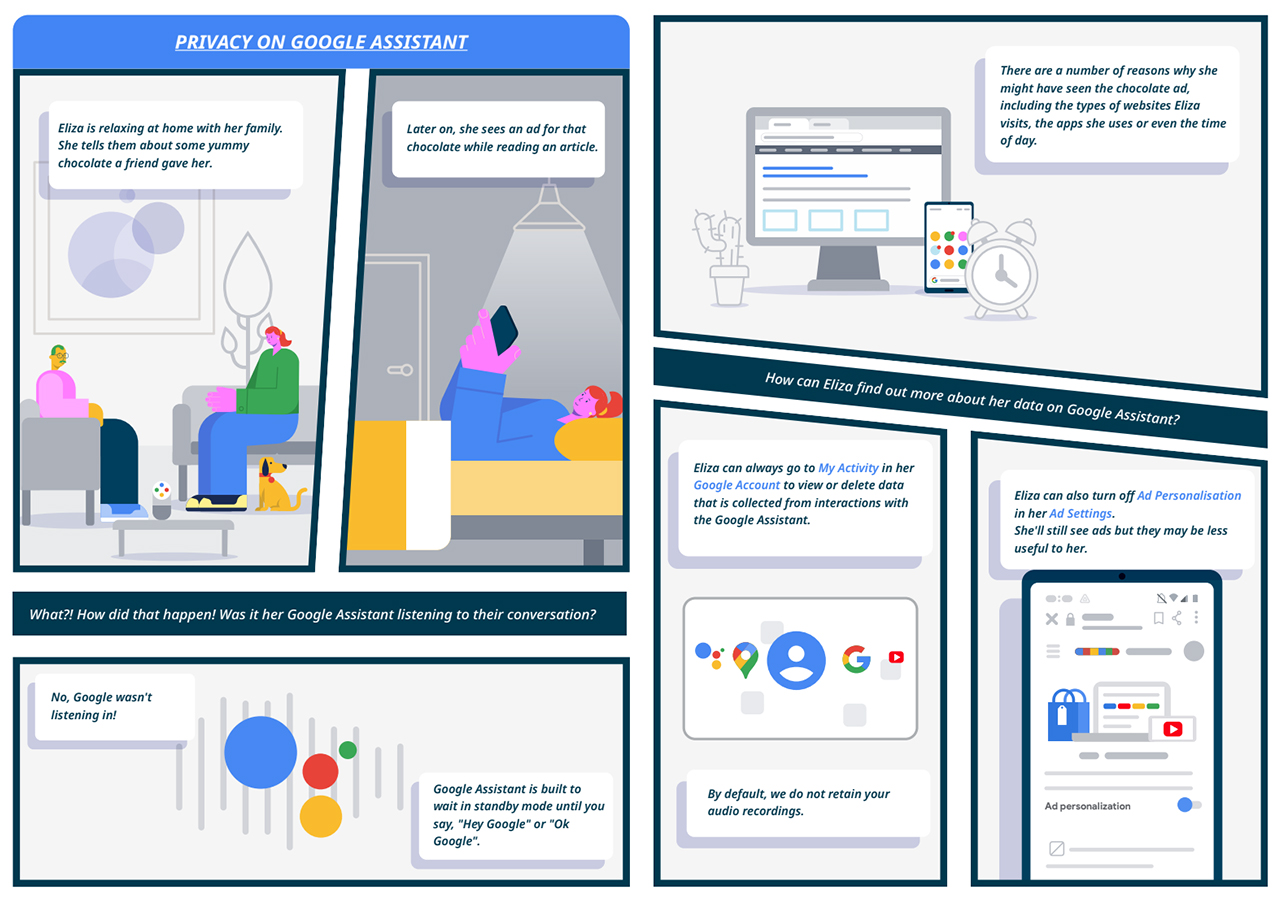
Google Assistant
Google Assistant, while looking like someone who spies on you, actually doesn’t save data even in standby mode. It only turns on when you command it with “Hey Google” or “OK Google”.
You can even ask it with “What data does Google collect?” or ask it to do something to protect your privacy such as “Delete what I just said” or “That wasn’t for you” — which results in having your most recent activity deleted. For further protection, you can view or delete data collected through My Activity.
How about ads?
Meanwhile, Google Search shows personalized ads that are only related to your Search query. Google doesn’t use private data such as email content, photos, document, or even sensitive information.
More importantly, ads are marked with labels like “ad” or “sponsored”, and only show up when there are useful ads related to the query.
A lot of us ask about seeing ads from our previous searches or topics we had in our conversations with friends — online and offline. So, is Google spying? Not really. According to Google, they’re not the only platform that utilizes data. Ads shown to you could’ve been the doing of other platforms that collects data. Plus, your cookies are partly to blame.
So, is our data safe and secure?
It’s safe to say that Google has an advanced security technology that protects users’ data, which automatically blocks a wide range of security threats such as government-backed attacks that could possibly be an attempt to obtain personal information.
Still, users have to take their part regarding responsible data practice. We can’t rely on the companies to do all the protection, we have to be cautious and secure our data as well, especially stuff that’s in our control.


Finding new vulnerabilities is part and parcel of a device’s lifecycle. Cybersecurity firms discover new holes in a device’s security regularly. Thankfully, a firm’s discovery quickly leads to a patch from the affected brand. A newly discovered one, however, is defying common practices. Apple has recently uncovered a hardware vulnerability that’s impossible to patch.
Recently, a team of researchers sprinkled throughout the United States brought the vulnerability to everyone’s attention. The potential exploit is present in Apple’s M-series, a recent lineup of chipsets for newer Macs.
The vulnerability works by exploiting a feature that complements the chipset’s memory called the data memory-dependent prefetcher (or DMP). The DMP can predict where a piece of code is based on previous behavior. It reduces the chipset’s latency, ensuring better performance.
Now, the exploit, which the researchers have named GoFetch, disguises itself as a “pointer,” which tells the DMP which data to fetch. GoFetch can effectively point at data it wants to steal, and the feature will hand the data over willingly.
In more practical terms, malicious parties can hide this exploit inside innocent-seeming apps. Though the exploit still needs a significant amount of time to work, it’s not impossible to trick users into having an illicit app open for an extended length of time.
The other catch is how impossible it is to patch. Because the exploit is a hardware-based vulnerability, Apple cannot patch it out without re-engineering the silicon. There are software-based patches; however, doing so will reportedly compromise the performance of the chipset. The team is still researching for the effects of other software patches.
At this point, the only way to protect against the vulnerability is the same piece of advice for all hacks: Be careful of what you install.
SEE ALSO: Apple M3 MacBook Air Review

According to Google, Filipino netizens had a higher interest in cybersecurity last year.
The Philippines ranked among the top in the world in keyword searches for the following terms:
- malinformation
- cybercrime
- phishing
- malware
- fraud
- scam
- one-time password
- password strength
The word “fraud” particularly reached a 13-year high in search volume. Meanwhile, searches for “scam” increased by 40% from 2022.
These keyword search trends are a reflection of the Filipino netizen’s better interest in internet safety practices.
To help more Filipinos maintain safe browsing online, here are eight tips from Google.
Install the latest OS, updates
Turn on auto-updates on your device and web browser. Don’t ignore warnings or notifications. It’s also crucial to run the latest updates for security enhancements and protection against new threats.
For Android device users, Google Play Protect should be automatically turned on to provide protection against malicious apps and more.
Use password manager
Google’s Password Manager is a free, built-in tool to help users create, store, and manage secure passwords for all accounts.
Aside from the convenience it gives, the service also analyzes saves passwords for weaknesses or if they’ve been exposed for breaches.
Secure accounts with passkeys
Speaking of passwords, Passkeys like fingerprints or face IDs provide an extra layer.
They can keep your accounts safe against phishing since they are stored on your device.
Run regular security checkups
Google Security Checkup is a simple tool within one’s Google Account that reviews and improves their online security.
This helps users identify and fix potential vulnerablities across digital properties from connected devices and third party apps.
Review your data settings
Run a deeper checkup to see whether your apps and accounts are above-board.
Make sure you’re not sharing any data, especially sensitive information. Look through each app and site as well to see if you agree with their terms and conditions, and settings.
Avoid suspicious links
Take a moment before clicking any online or SMS links. These are usually links that can steal your sensitive information.
If a link does not look legitimate, report them immediately and block the source.
Don’t give in to pressure
Scams and frauds, whether online, over the phone, or in person, rely on pressuring someone or getting them nervous and careless.
When you are rushed to make a decision and it feels unusual, take a moment to stop, think, and assess the situation. If you’re not allowed to pause, something is not right.
Check the facts
Before posting or sharing, verify information first. See if the information is from a trusted source. Using Google Search, check the way it is written or said, who shared it, and other details.

Over the years, Chrome’s Incognito Mode accumulated quite the reputation. For most users, the alternative browsing mode was a quick way to browse dubious websites away from prying eyes. However, the mode isn’t as incognito as the name implies, as evidenced by a lawsuit from years ago. Now, Google has caved in and admitted the shortcomings of Incognito Mode.
Back in 2020, Google faced a lawsuit against the purported security of Chrome’s Incognito Mode. The lawsuit alleges that the private mode still lets websites track a user’s data.
At the time, Google themselves confirmed that websites can do that. Now, almost four years after the lawsuit, the company has agreed to settle the US$ 5 billion lawsuit.
Now, Chrome is adding a new disclaimer (spotted via MSPowerUser) to hopefully keep users from expecting complete privacy while using Incognito Mode. Besides alerting users that the device still saves downloads and bookmarks, the disclaimer that shows up whenever Incognito Mode is opened now also reads: “This won’t change how data is collected by websites you visit and the services they use, including Google.”
Unfortunately, the disclaimer isn’t meant to change how websites process your data. It’s just a way to reduce Google’s liability whenever someone complains about the security of their data.
Now, if you’re looking for a more secure way to browse the internet, other methods will serve your purposes more. For example, VPNs and Tor offer more anonymity online. Some browsers — Brave, for instance — offer those services built into the software already.
SEE ALSO: Google sued for tracking Chrome users in Incognito Mode
-

 Features2 weeks ago
Features2 weeks agoFortify your home office or business setup with these devices
-

 Reviews1 week ago
Reviews1 week agorealme 12+ 5G review: One month later
-

 Gaming2 weeks ago
Gaming2 weeks agoNew PUMA collection lets you wear PlayStation’s iconic symbols
-

 Accessories1 week ago
Accessories1 week agoMarshall Major V: Reasons Why I Love It
-

 Gaming2 weeks ago
Gaming2 weeks agoMore PlayStation 5 Pro specs have been leaked
-

 Features1 week ago
Features1 week agoWhy choose the MSI Claw?
-

 Gaming2 weeks ago
Gaming2 weeks agoUbisoft is taking away copies of The Crew from your library
-

 Gaming2 weeks ago
Gaming2 weeks agoOne Piece Odyssey coming to Nintendo Switch