News
Samsung Galaxy S9+ takes top spot on DxOMark
Beats the Pixel 2 and iPhone X

One of the biggest questions on everyone’s mind whenever a new smartphone launches is, “How good are the cameras?” While it’s often subjective and difficult to gauge from early photo samples, imaging authority DxOMark’s numeric ratings provide a good idea of where a handset’s cameras stand.
The latest entry is Samsung’s Galaxy S9+. It launched during Mobile World Congress earlier this week and is the first Galaxy S smartphone to own dual cameras of any sort. The setup turned out well for Samsung, as the cameras have been bestowed the highest rating ever on DxOMark’s mobile scoring.
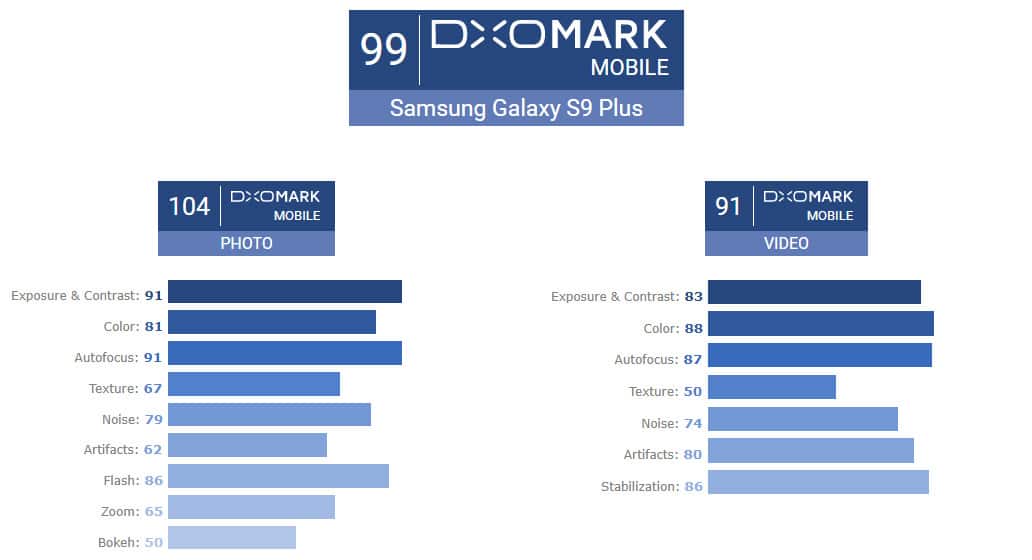
With an overall score of 99, the Galaxy S9+ is a point higher than the previous king, the Pixel 2, and two points above the 97 of the iPhone X and Mate 10 Pro. That’s an impressive feat considering how strong the competition was during our own camera shootouts.
Here’s the breakdown of the numbers:
Where the Galaxy S9+ truly shines is in the still photos department. Its 104 points are way above the previous top score of 101 by the iPhone X. Meanwhile, the 91 video score is quite good, too, losing only to the 96 of the Pixel 2.
DxOMark praises the Samsung flagship for having no real weakness. The Galaxy S9+ is strong in all aspects, and performs well in any lighting situation. Other advantages are the secondary lens on the back for optical zooming (something the smaller Galaxy S9 doesn’t have) and a true portrait mode that blurs out the subject’s background.
But before Samsung can celebrate, they have to accept that it’s still early in 2018. With flagships from Huawei coming out soon and both Google and Apple releasing even better smartphones later this year, these rankings can easily turn to another’s favor.
We’ll have to get the Galaxy S9+ in our hands for a full review before we can attest to these scores. Stay tuned for that.

Accessories
Logitech introduces a dedicated shortcut for ChatGPT
Compatible with most keyboards and mice

Artificial intelligence is already meant to simplify a workflow. However, despite the ease, there are still a few ways to optimize the process. Today, Logitech has launched a new shortcut to launch ChatGPT straight from your mouse or keyboard.
Minus programmable hotkeys or buttons, there are hardly any built-in way to easily access an AI model. For a typical workflow, it still consists of manually opening the model on a separate window and keeping it within cursor’s reach throughout the day.
Logitech is simplifying the process by adding a dedicated shortcut for its devices. With a Logitech keyboard or mouse supported by the Logi Options+ app, users can program a keyboard or mouse button for the new Logi AI Prompt Builder.
Once activated, the AI Prompt Builder automatically accesses easy options for highlighted text. For example, users can easily rephrase or summarize the text. Likewise, they can input their own custom queries. By eliminating a few clicks and some typing throughout the day, the new tool hopes to save you time.
While most Logitech keyboards and mice are compatible with the new tool, it is also more easily accessible with the new Logitech Signature AI Edition Mouse. The new mouse has a dedicated button just for AI prompts. If you’re an AI power user, this one is perfect for you.
SEE ALSO: Logitech unveils G Pro X 60 gaming keyboard: Price, details

Despite the ease that the technology promises, artificial intelligence still isn’t the most reliable thing you can depend on. Today’s models can still flub answers. Now, the pitfalls of AI are abundantly clear with a few mishaps on X. Golden State Warrior Klay Thompson was just “accused” of a vandalism spree involving bricks.
Late Tuesday night, X presented an AI-generated news snippet. The article, posted soon after the Warriors’ play-in loss to the Sacramento Kings, reads: “Klay Thompson Accused in Bizarre Brick-Vandalism Spree.”
The snippet hilariously described an incident where Thompson supposedly vandalized houses in Sacramento with bricks. Thankfully, according to the snippet, no one was hurt. It even had a few sources for its claims below the news summary.
First off… I am ok.
My house was vandalized by bricks 🧱
After my hands stopped shaking, I managed to call the Sheriff…They were quick to respond🚨
My window was gone and the police asked if I knew who did it👮♂️
I said yes, it was Klay Thompson
— LakeShowYo (@LakeShowYo) April 17, 2024
The sources, however, are just joke posts stemming from the recently concluded game. In that do-or-die game, Thompson put up a staggering 0 points on ten shot attempts, the most misses without a make by a Warrior since the ’68 season. Naturally, everyone joked that the Warriors guard just threw bricks all over Sacramento.
Now, X is currently experimenting with a new AI feature called Grok. The model collates trending topics and creates snippets of what’s happening for X users. However, it’s not exactly the smartest in determining real news from satiric ones. The feature notes as much, carrying a fine-print caveat warning users to “verify its outputs” because it’s an early feature and can make mistakes.
SEE ALSO: New X users must pay a dollar per year to post and reply
New users on X might soon face a tough time on the platform. The social media website will likely start charging new accounts a small fee for the right to post on the platform.
Now, the fee isn’t a new one. Almost six months ago, the company tested the paid system in New Zealand and the Philippines. New users in those countries had to pay a dollar per year for the ability to post and reply to content.
As spotted by X Daily News on the same platform, the company might be ready to take the experiment to a larger market. New text strings have shown that the policy is rolling out worldwide.
SPECULATION: X might be expanding its policy to charge new users before they reply/like/bookmark a post https://t.co/odqeyeiHBx pic.twitter.com/EU71qlwQ0D
— X Daily News (@xDaily) April 15, 2024
The policy is designed to combat a wave of bots appearing on the platform. By preventing new accounts from creating posts, X hopes to stave off the standard behavior of bots these days. You might have noticed them as OnlyFans creators in unrelated posts, peddling NSFW content on their bio.
Though the global rollout was only just spotted, owner Elon Musk has seemingly confirmed the change. Replying to X Daily News, Musk says that it is “the only way to curb the relentless onslaught of bots.” He says that the current breed of bots can easily bypass simple checks these days.
-

 Accessories2 weeks ago
Accessories2 weeks agoApple Vision Pro Review: Two Months Later
-

 Features5 days ago
Features5 days agoFortify your home office or business setup with these devices
-

 Gaming1 week ago
Gaming1 week agoThe Rogue Prince of Persia looks like an ultra-colorful roguelite
-

 Events1 week ago
Events1 week agoStellar Blade: PlayStation taps cosplayers to play Eve for game’s launch
-

 Gaming1 week ago
Gaming1 week agoStar Wars Outlaws release date revealed
-

 Accessories1 week ago
Accessories1 week agoLogitech unveils G Pro X 60 gaming keyboard: Price, details
-

 Philippines2 weeks ago
Philippines2 weeks agovivo Y100 to release in Philippines on April 27
-

 Deals2 weeks ago
Deals2 weeks agoSamsung Awesome April: Deals on Galaxy A series